Background
We can all agree that ransomware is a pervasive threat that impacts all organizations regardless of industry or size. Ransomware attacks have evolved from the early, commodity, non-targeted, automated, mass distributed attacks of a decade ago to more targeted and sophisticated attacks primarily carried out by criminal organizations with monetary gain the prime motivator.
Today cybercriminals use a combination of people and tools to move across the kill chain and execute a mission, which often includes both encryption and data theft. While these attacks can still rely on phishing or drive-by downloading to deliver malware, they increasingly include the use of compromised-credential dumps, password-spray attacks, previously compromised endpoints, and the exploitation of unpatched or poorly secured internet-facing resources.
So how do you defend against the latest ransomware threats? Like the punchline to the joke where you don’t have to outrun the bear, just the person you’re with, you need to make it harder and more expensive to attack your organization than others. When cybercriminals realize the return on attacking you is not profitable, they will turn to other, less secure organizations. Designing and operating your tenancy more securely will result in making it a less attractive target, help reduce the likelihood of a successful attack and minimize the potential impact of a breach.
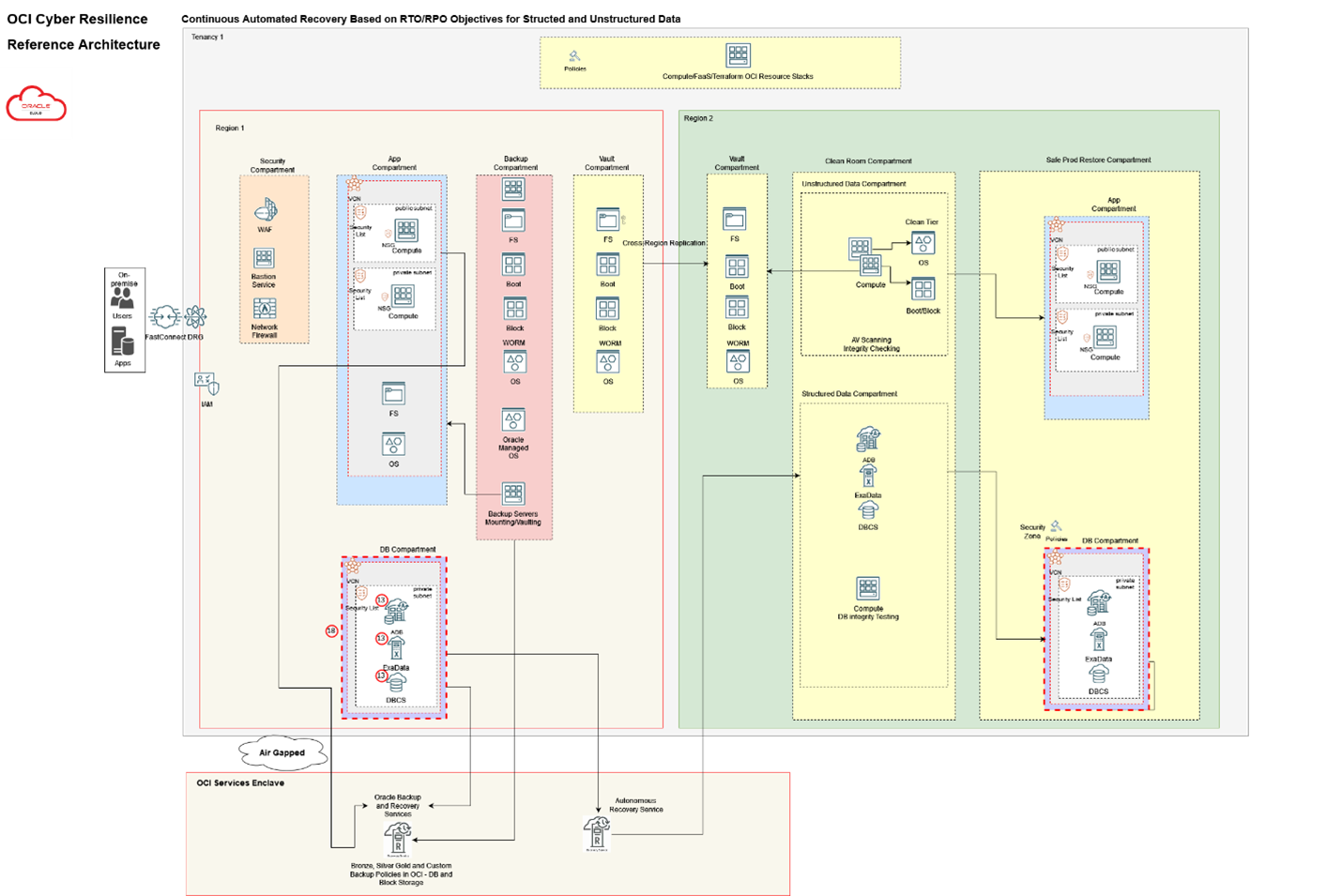
In this first in the series of blogs on how OCI customers can use native services and capabilities to address the ransomware threat we will explore protecting your tenancy against attack. Follow on blogs will cover OCI capabilities to help detect potentially malicious behavior and signs of an attack, and finally, preparing for and executing a recovery in the event of a successful attack. The image below image shows all of the components that will be covered in this series in a reference architecture.
All the concepts covered in this and future blogs in this series are included in the OCI CIS Secure Landing Zone. The Landing Zone is a set of Terraform modules designed to assist you in creating a tenancy that meets the requirements in the CIS Foundations Benchmark for OCI and includes Oracle best practices around many of its services. Refer to https://docs.oracle.com/en/solutions/cis-oci-benchmark/index.html#GUID-4572A461-E54D-41E8-89E8-9576B8EBA7D8 for details on the Secure Landing Zone.
Common Attack Profile
An attacker needs two things to compromise your tenancy, access, and time. Exploiting compromised credentials or unpatched Internet facing infrastructure and/or applications is the most common way attackers gain access to your environment. There are also a host of other methods that we will explore throughout the series. Once an attacker gains access to a tenancy, they attempt to move laterally through the environment via both logical access permissions and network level access. They use lateral movement to work their way through the environment to find the systems and applications that give them access to your sensitive data. To help prevent this you need to limit lateral movement at both the logical access and network layers.
Attacks unfold in three stages: Recon, Weaponize, & Deliver; Exploit & Control; and Execute & Maintain. As a defender, you have opportunities to thwart attacks at each stage as depicted below.
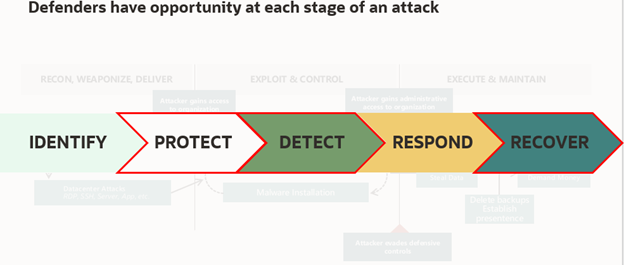
OCI provides several services and capabilities that can be leveraged to help Protect, Detect and Recover from ransomware attacks. These are included in the reference architecture shown below and will each be discussed in more detail throughout the series.
Logical Protection
Carefully designing the compartment structure of your tenancy to provide isolation of critical workloads and data and allow for distributed administration of your cloud resources provides a solid foundation for enforcing least privilege access and separation of duties.
Grouping your cloud resources to align with your operational model allows you to distribute and limit administrative privileges based on role and limiting full tenancy administrative rights to a break-glass model.
- For instance, only allow your networking team to manage the networking components while limiting database management to a DBA team.
- The tenancy admin privilege should be restricted to a very few accounts that are vaulted, highly restricted, closely monitored and not used in normal daily activities.
The OCI IAM policy engine is easy to use and understand and allows you to create extremely granular policies to limit access. An example is allowing a group the ability to create and manage object storage buckets, commonly used to store backups, but not allowing them to delete objects or buckets.
- Allow Storage_Admins to manage buckets in {tenancy OCID} where request.permission != ‘DELETE’
Separate identity domains can be assigned to control access to specific compartments. For example, you can create a “vault” compartment that you use to store copies of buckets, block volumes and manual database backups and assign a separate identity domain to control access. This results in not allowing anyone who has access to the main environment to use the same credentials to access the vaulted compartment, providing isolation and protection of these assets.
The next step is securing all accounts that have access to OCI using multifactor authentication (MFA). This includes both federated and local OCI accounts.
- Federated accounts are typically controlled through identity providers including Microsoft/Azure Active Directory, Ping or Okta who all have multiple methods for enforcing MFA.
- OCI IAM also supports multiple methods for enabling MFA including Security Questions, Mobile App Passcode, Mobile App Notification, Text Message (SMS), Email, Bypass Code, and Duo Security.
You define policy to control how MFA is enabled that can include multiple conditions, risk factors and actions to further strengthen user authentication. Enabling MFA for all federated and local OCI accounts makes it significantly more difficult for an attacker to compromise an account and access your tenancy.
Network Protection
On the network front, you need to do all you can to prevent an attacker from gaining access to your network and disrupt them from moving laterally within your tenancy. OCI provides multiple capabilities to do help you implement controls to achieve a secure network. There is no network access to your tenancy by default. You must implement services to allow for ingress/egress and specify the direction and ports/protocols allowed. The base for all networking in OCI is the Virtual Cloud Network (VCN). By separating systems containing sensitive information, including databases, into their own VCNs, you can granularly control access between and within a VCN achieving the first layer of segmentation.
Further segmentation and isolation can be achieved between subnets and cloud resources via the use of Security Lists (SL) and Network Security Groups (NSG). Security Lists operate at the subnet level and control ingress and egress for the subnet. NSGs provide isolation at the VNIC layer and allow you to implement micro-segmentation between individual VNIC equipped resources.
The Network Firewall service can be configured to provide traffic filtering and monitoring between your tenancy networks and the Internet, your own internal network and between and within VCNs and subnets, further strengthening the segmentation of your network and reducing the ability for an attacker to access and move laterally through your overall cloud network environment.
OCI also provides gateways that enable Internet ingress/egress. The Internet Gateway allows ingress traffic with the NAT gateway enabling egress. Both can be locked down in a variety of ways to restrict traffic and provide a more secure perimeter. You can also configure a FastConnect connection between your tenancy and your internal network and require all traffic to/from the tenancy traverse your network security stack. This turns your OCI tenancy into effectively a private enclave where control all network access via a single connection. FastConnect is a layer 2 connection and can be configured with MACsec encryption to provide additional security.
Infrastructure and Application Protection
OCI provides several capabilities for protecting the infrastructure resources in your tenancy. These include:
- OCI provides default DDoS protection against volumetric attacks, and we have solutions for providing Layer 3 and 4 protection as well.
- Fronting your public facing applications with the OCI WAF provides protection against many web-based attacks.
- Vulnerability management can be achieved through the combination of the Vulnerability Scanning (VSS) and OS Management (OSM) Services. VSS can scan all your compute nodes and containers for both open ports and CVSS based vulnerabilities. OSM provides a way to identify missing OS and security patches and to automate patching across your Oracle Linux and Windows compute nodes.
- IAM policies can be configured to remove the ability to delete storage (Object, Block and File) and backups and limit tenancy administrative rights to a break glass account that can be vaulted.
- Making your storage immutable and therefore resistant to ransomware
- Enable versioning on Object Storage buckets
- Oracle managed backups for block volumes and Oracle database services renders these immutable and they are stored in a separate, Oracle controlled enclave that allows no direct connectivity from your tenancy.
- OCI Vault provides an HSM backed, full lifecycle management service for keys and secrets if you want to manage your own encryption keys.
- Security Zones can be defined to provide guardrails for the creation and movement of cloud resources that include preventing the creation of public buckets, assignment of public IP addresses, require that customer managed encryption keys be used to secure all storage and many more.
Conclusion
Protecting your tenancy from unauthorized access and limiting access for both management of cloud resources and at the network layer form the protective foundation for a successful ransomware mitigation strategy. The infrastructure and application protection capabilities further harden your tenancy against compromise. OCI provides several services and capabilities that can assist you in properly securing your tenancy against these threat vectors. Using these services and capabilities can’t guarantee that your tenancy is immune from compromise as there is no such thing as perfect security and the cybercriminals are constantly improving their tactics and techniques. They only need to get it right once to get in, while you have to be perfect all the time to keep them out. The next blog will address the ability of OCI to help you find and get notified of potentially malicious behavior in the event you experience a breach. (See Detecting Signs of Ransomware Style Threats in your Tenancy). The final blog in the series will detail how OCI can help you prepare for a recover from a successful ransomware attack. (See Recovery from Ransomware Style Threats).
This blog covered a lot of ground and touched on several services and capabilities available natively within OCI to help you protect your tenancy. For more information on these, please refer to OCI’s public facing documentation here: https://docs.oracle.com/en-us/iaas/Content/GSG/Concepts/baremetalintro.htm. For details on all OCI services follow this sub link from the above: https://docs.oracle.com/en-us/iaas/Content/services.htm.
