Overview
Update March 2025: Some aspects of this architecture will change with the Oracle Fusion Identity Upgrade—details available here. We will update this document accordingly once the upgrade begins.
Oracle Fusion Cloud Supplier Portal is a great option for many of our customers to connect with their suppliers. However, opening to users outside their organisation can introduce additional risks that should be mitigated by reviewing and rolling out additional security measures. For many organisations Multi-Factor Authentication (MFA) is the Gold Standard to improve authentication security and protect against stolen identities or worse. As described in the base article “Securing Oracle Fusion Cloud Applications with Multi-Factor Authentication (MFA)” Fusion Applications implements MFA via IAM Domains.
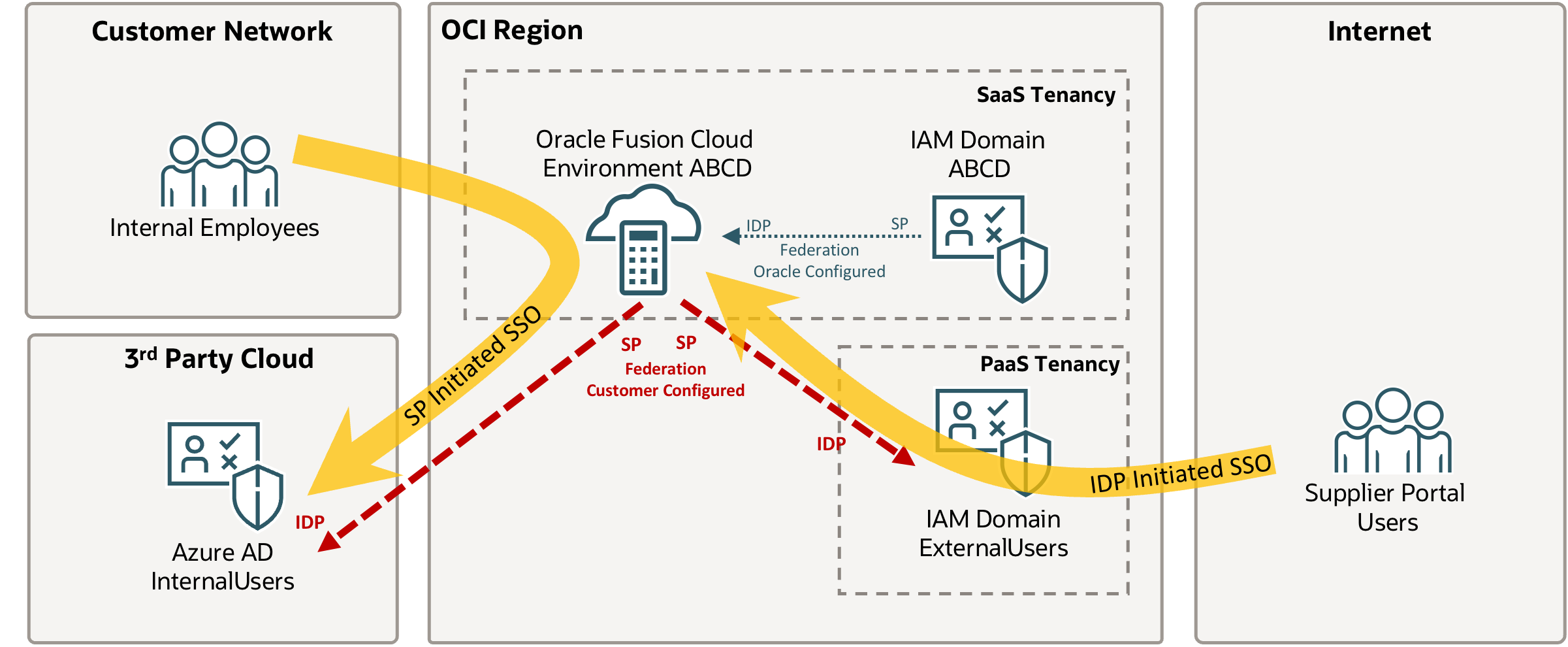
Described in this blog is a scenario that we encounter at many customer sites: Existing employees / internal users are authenticated on the Fusion Cloud via MS Azure AD / Microsoft Entra ID. The Azure AD Authentication is configured as Service Provider (SP) Initiated SSO and has been setup for a while. Existing login flows should not be affected by the introduction of Supplier Portal and MFA. This is not necessarily the optimal setup for every architecture, but is very common – the setup is described here.
In this architecture all Supplier Portal Users are created in the Fusion Cloud – see “How Supplier User Provisioning Works” Chapter in the documentation for details. Afterwards they are synchronised and can authenticate via the additional IAM Domain ExternalUsers with enforced MFA to separate external from internal users. This deployment improves the separation of users and allows separate rules for example for IP based rules for authentication. This could for example be configured so that Supplier Portal Users are only allowed to authenticate from specific IP addresses – this is implemented using Network Perimeters.
Prerequisites
Review and setup the Supplier User Provisioning process as described in the documentation. Make sure Suppliers are created as expected before moving on to this blog setup. This configuration will sit transparently on top of the Supplier User Provisioning process, so if you already have Supplier User Provisioning in place the Procurement employees don’t have to change their processes to setup Supplier. This works with the Supplier Self-Service Registration.
Validate that the existing IDP is Azure AD / Entra ID and the corresponding setup is up and running as described here. This deployment will also work with other IDPs and Azure AD via IAM Domain setups. It will however not work with the bypass of the Federated SSO Login for Supplier portal solution – please raise a ticket to disable the bypass if you had previously requested it.
The next step is to create an IAM Domain and wire it with Fusion Applications as described here: https://www.ateam-oracle.com/post/securing-oracle-fusion-bill-management-with-iam-domains
Configuration
First review and define which users you would like to have access to the Oracle Fusion Applications Supplier Portal via the new IAM Domain – the management of Supplier Roles is described here.
These could be for example:
Supplier Accounts Receivable Specialist ORA_POS_SUPPLIER_ACCOUNTS_RECEIVABLE_SPECIALIST_JOB
Supplier Contract Administrator ORA_OKC_SUPPLIER_CONTRACT_ADMINISTRATOR_JOB
Supplier Inventory Manager ORA_INV_SUPPLIER_INVENTORY_MANAGER_JOB
Supplier Product Administrator ORA_EGS_SUPPLIER_PRODUCT_ADMINISTRATOR_JOB
Supplier Sales Representative ORA_POS_SUPPLIER_SALES_REPRESENTATIVE_JOB
Supplier Self Service Administrator ORA_POS_SUPPLIER_SELF_SERVICE_ADMINISTRATOR_ABSTRACT
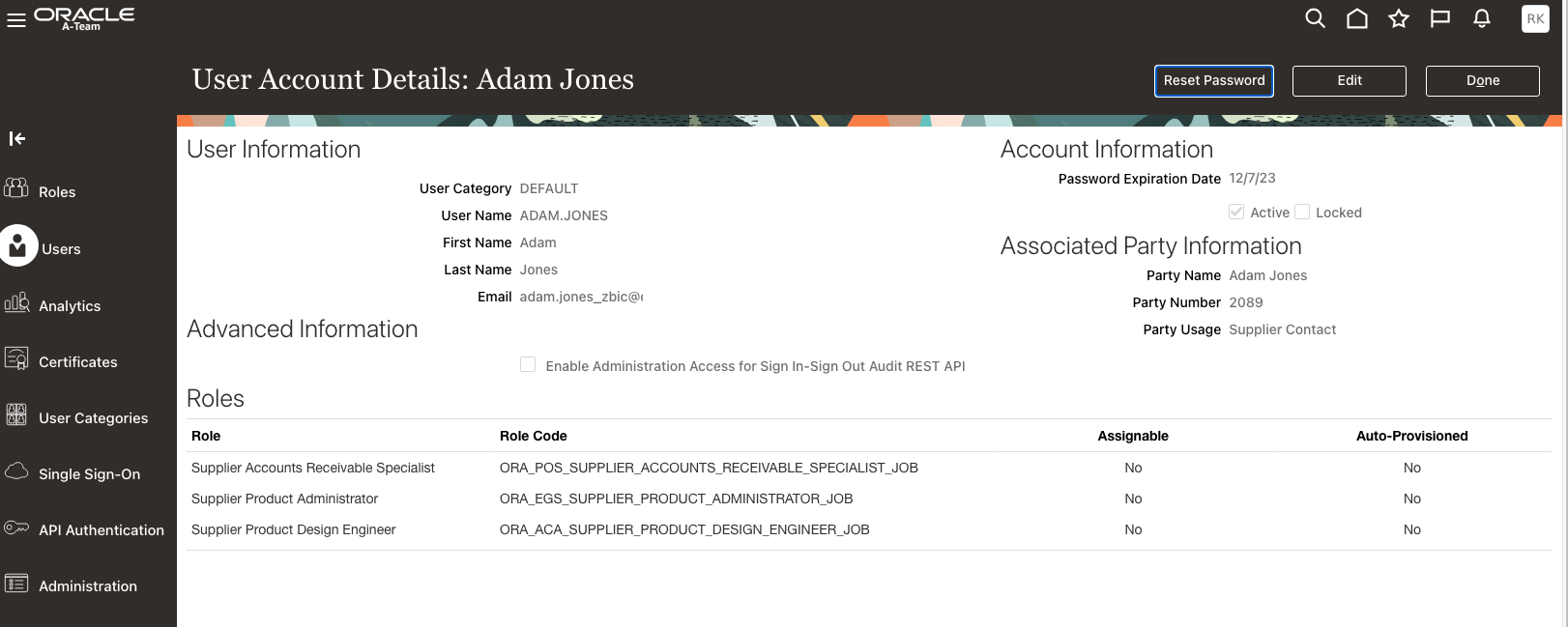
For easier troubleshooting its suggested to validate using a sample supplier account – this blog chooses Adam Jones in this case – review that the user has at least one of the roles that is supposed to be used for synchronisation.
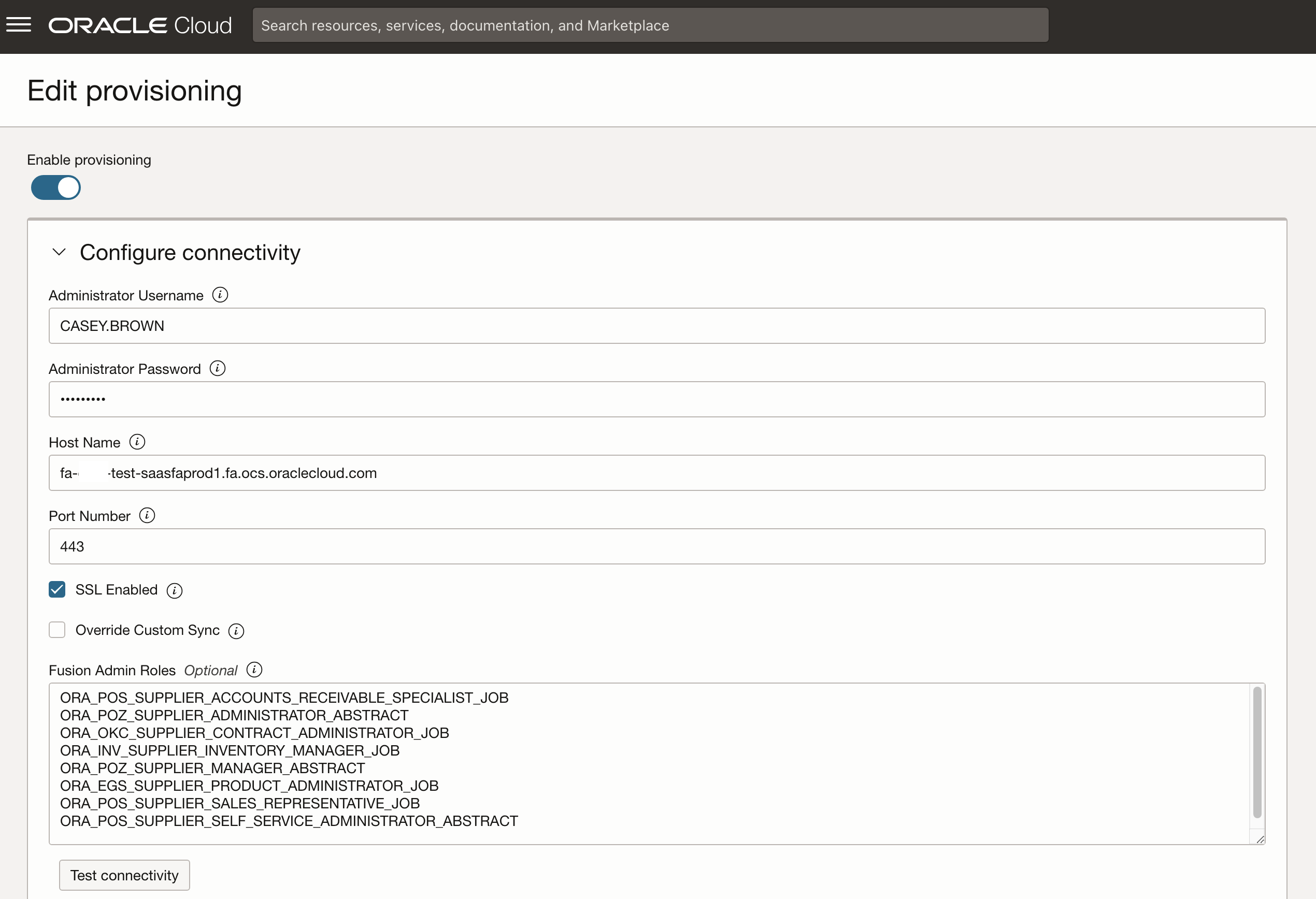
If you are looking to sync these roles go into the newly created domain and edit the provisioning setup as shown below, given there are multiple roles – specify each of the new roles on a separate new line as shown. Ensure to deselect the “Override Custom Sync” checkbox as this will otherwise sync all users.
Ensure that Authoritative Sync is enabled so that accounts are only allowed to be created from Fusion Application and not from IAM. This ensures that all Supplier Users must be created in the Fusion Cloud and cannot just be created in IAM to avoid mismatches. See https://docs.oracle.com/en-us/iaas/Content/Identity/applications/enable-provisioning-app-catalog-application.htm
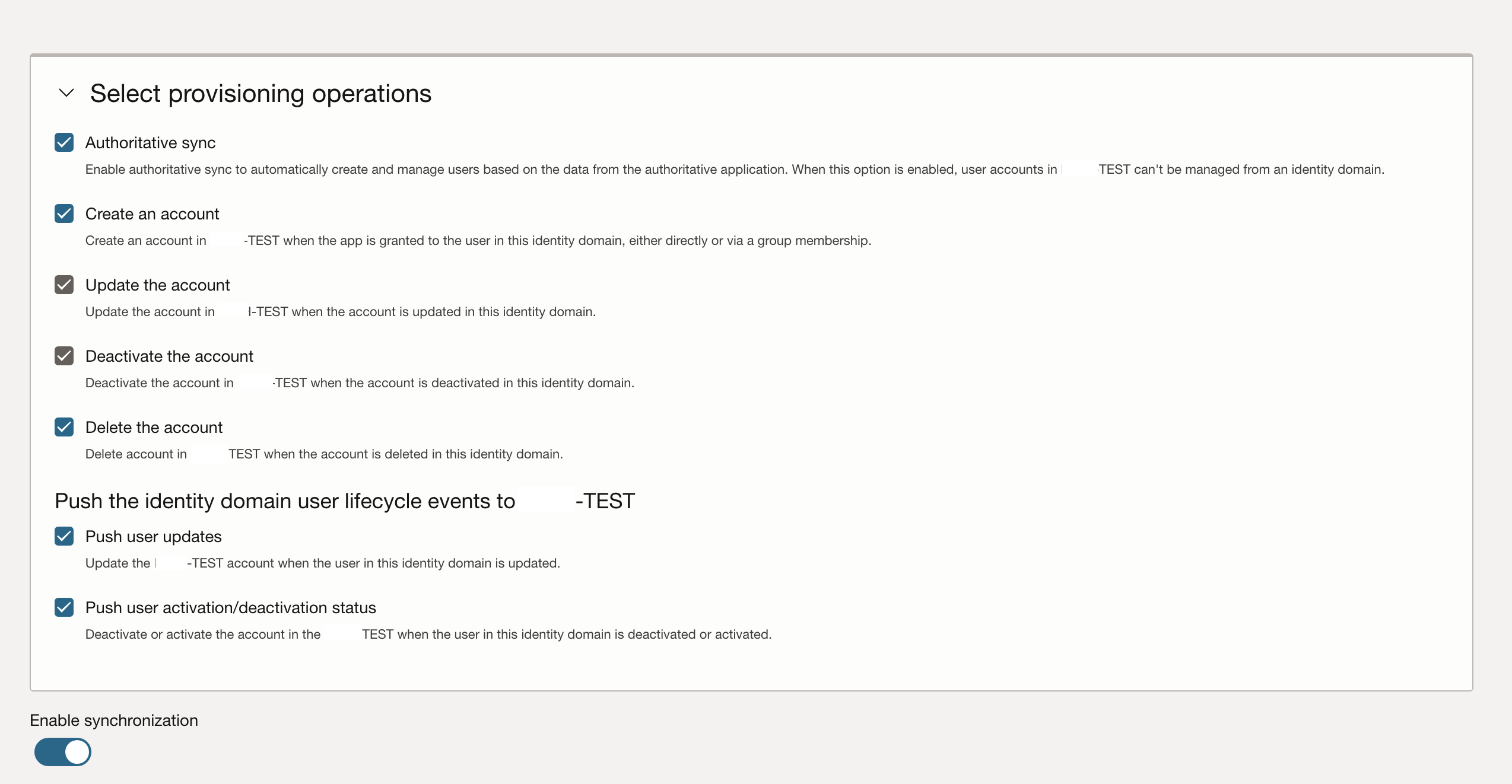
Configure the synchronization to match your requirements – please note that if e.g., one hour is selected as frequency, new accounts get created once an hour and before that no access is available.
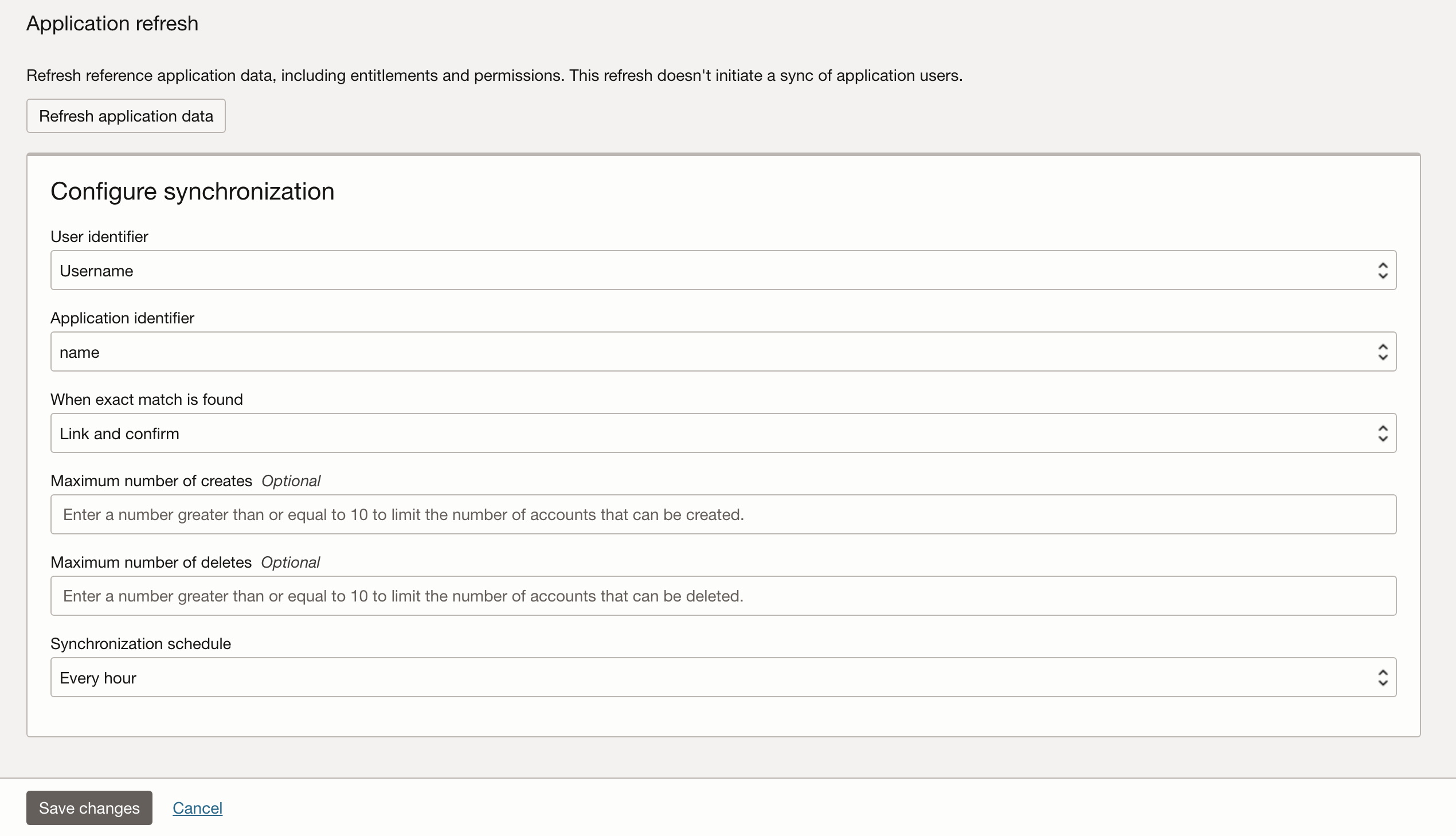
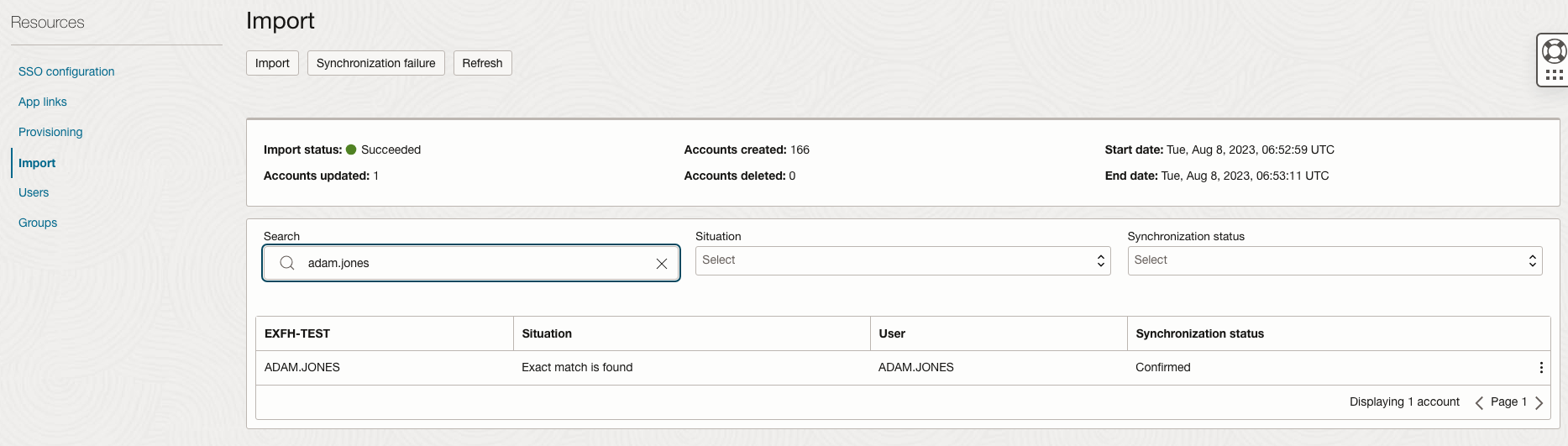
Navigate to the Import section of Application and validate that the example user is synchronised as expected below.
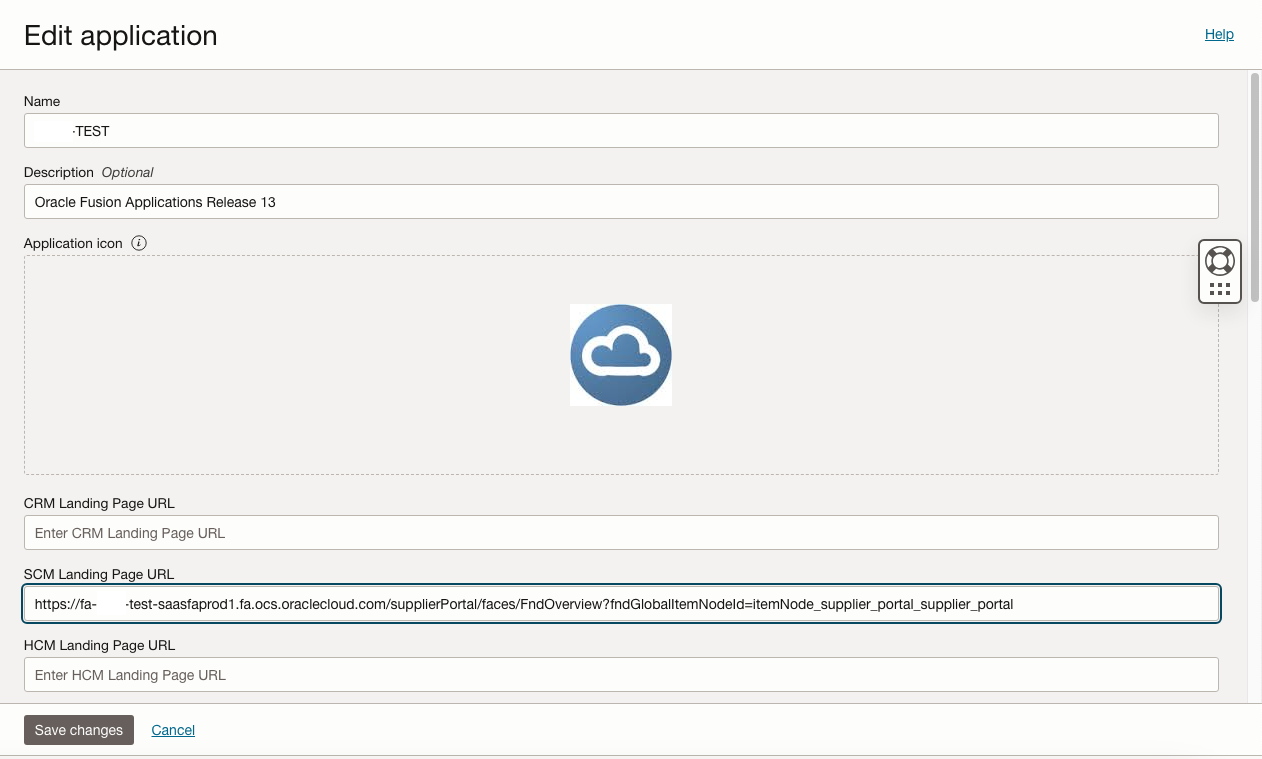
Next edit the Application that has been created as part of the IAM Domain creation above and set the SCM Landing Page to the URL of the Supplier Portal URL.
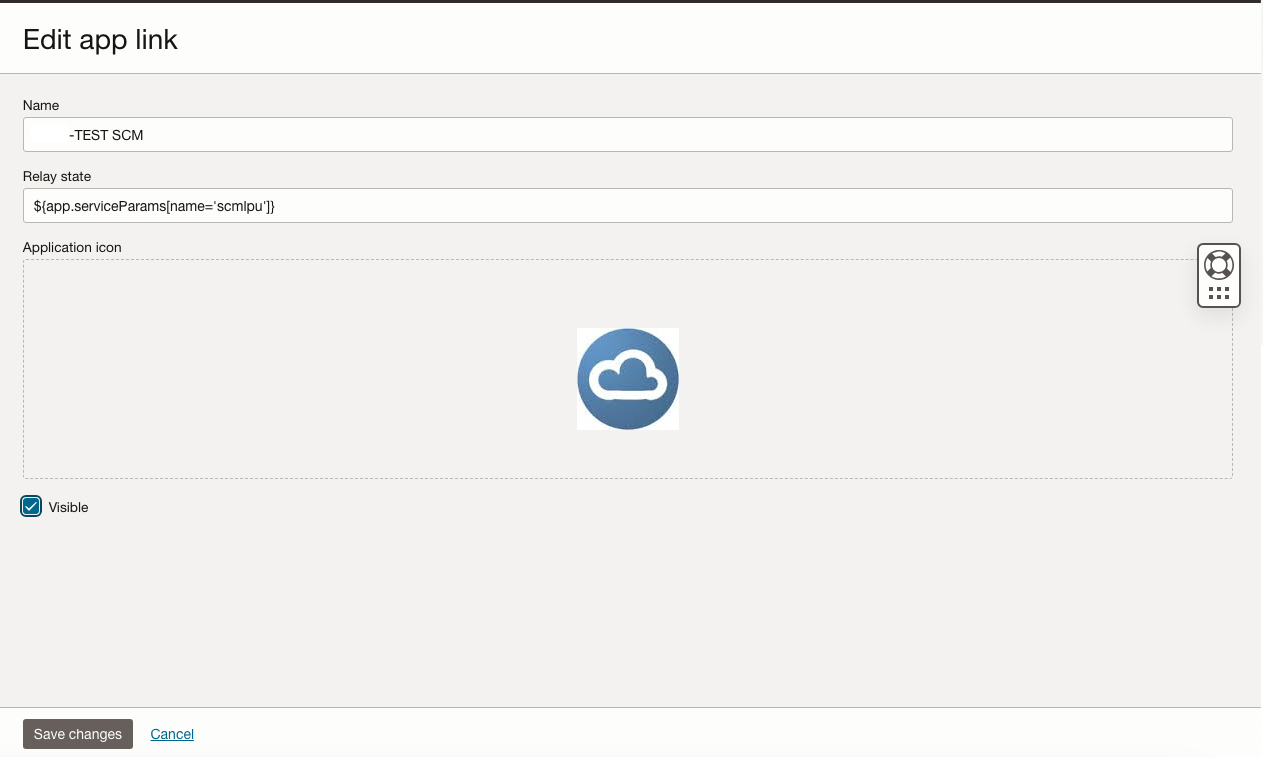
Ensure the App is marked as Visible and Save the Changes. This refers only to the visibility of the App in the Console as shown below.
IdP Initiated SSO
The easiest way to retrieve the URLs for the IdP Initiated SSO is via the IAM Domain Console. Go to the Domain Homepage of the external IAM Domain and copy the Domain URL.
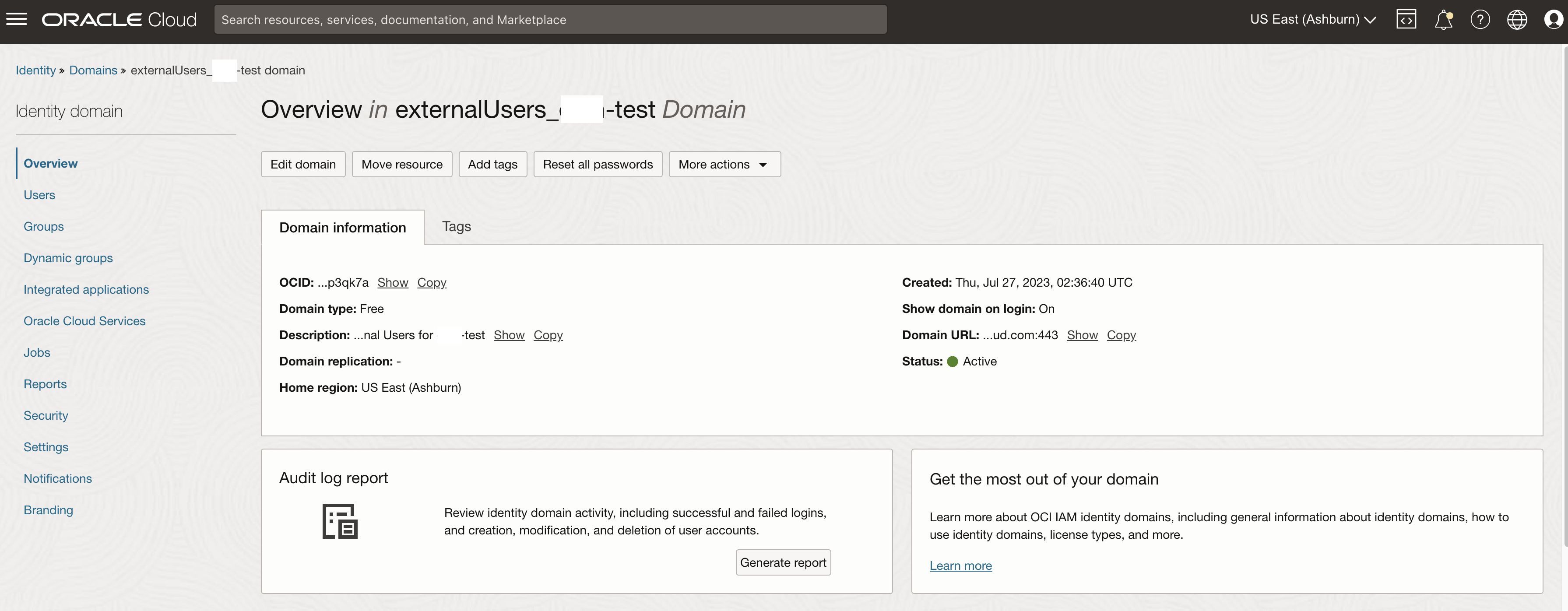
Next retrieve the IDP Initiated SSO URL – to achieve this add /ui/v1/myconsole to the end of the URL copied above similar to: https://idcs-XXXXXXXXXXXX.identity.oraclecloud.com:443:/ui/v1/myconsole
Login with the Sample user as above to get to the following window – this console shows all apps available for the user – copy the linked to the app you want internal users to use. This is the URL for the IdP initiated Login via the External IAM Domain created above and will look like:
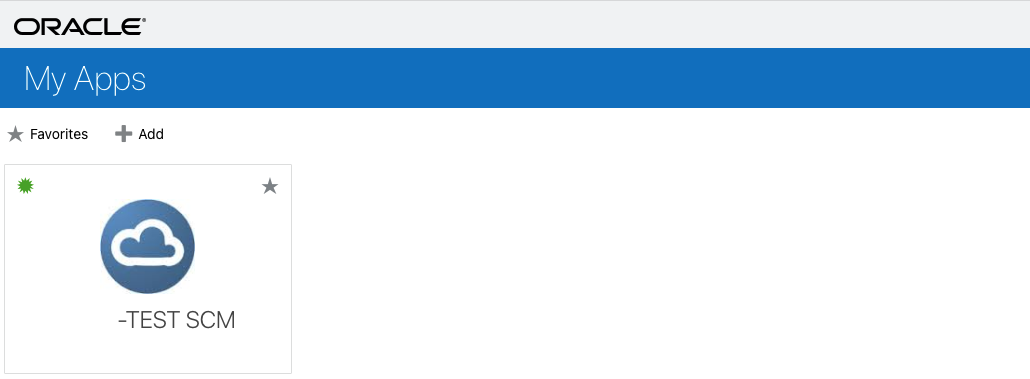
MFA Configuration
Follow the steps to configure MFA in this article in the section MFA Configuration
Opening the Link will trigger the IDP Initiated SSO. This is the link that Suppliers will use to login to the Supplier Portal.
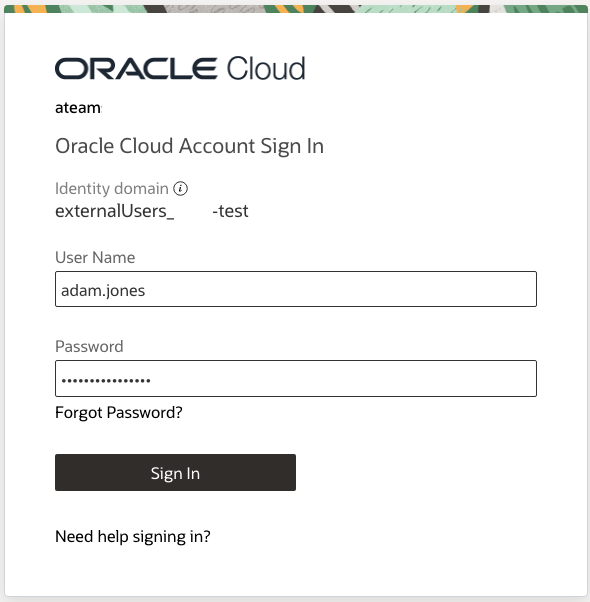
If MFA is setup correctly the setup now triggers the MFA enrolment screen for the user. The users will not be able to proceed without enabling the MFA configuration.
Once configured a normal MFA flow for a regular login attempt into Fusion – here the users approve the access on his previously enrolled iPhone.
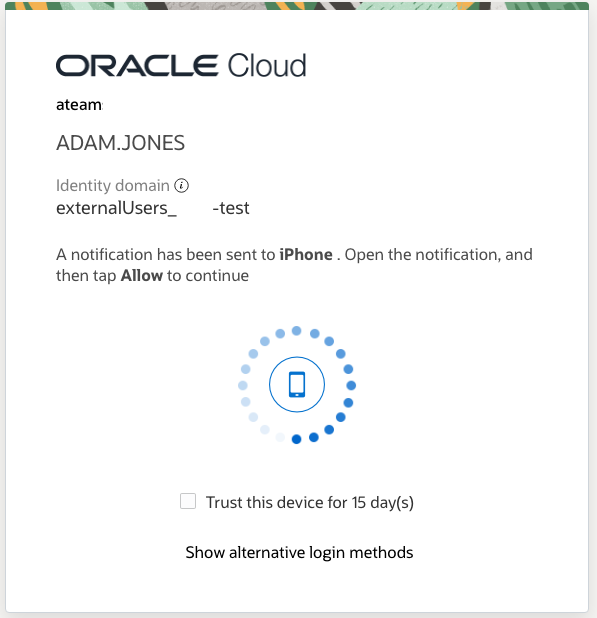
Once authenticated the User will be directed to the Supplier Portal.
This blog only covers a subset of the technical possibilities to secure Oracle ERP Cloud. Make sure to review the latest “Securing Oracle ERP Guide” – https://docs.oracle.com/en/cloud/saas/applications-common/23d/faser/securing-oracle-erp-cloud-overview.html#s20058418
Notifications
An important part for each implementation is to make sure that only the right notification emails with the correct links are sent out to avoid confusing users. Keep in mind that the passwords between the local Fusion users, the IAM Users and other IDPs are not syncronised, so make sure that especially new users do not get notifications about changing their local Fusion password if they are supposed to be using their IAM password for the IDP initiated SSO.
Enable the notifications for newly syncronised users from IAM as described here: Notifications Not Sent from IDCS for New Created Users In IDCS While the Users Are Sync’ed from Fusion App (Doc ID 2652989.1) Make sure to use PATCH and not POST in the curl call. Customise the notification to your requirements as described here – consider including the IDP initiated SSO link for easy login.
Make sure the new user notification for Suppliers Users in Fusion is disabled through the “Configure the New Supplier Notification” option – make sure to customise and test the other notifications to avoid confusion.
Further Reading
FAQ on features in Fusion Supplier Portal (Doc ID 1324616.1)
Securing Oracle Fusion Cloud Applications with Multi-Factor Authentication (MFA)
